A few decades ago, securing a car meant a sturdy lock and an alarm. Today, it means defending a rolling, always-connected computing platform – equipped with dozens of Electronic Control Units (ECUs), multiple in-vehicle networks, and high-speed links to the cloud.
A few decades ago, securing a car meant a sturdy lock and an alarm. Today, it means defending a rolling, always-connected computing platform – equipped with dozens of Electronic Control Units (ECUs), multiple in-vehicle networks, and high-speed links to the cloud.
In this new landscape, the High Performance Computer (HPC) is becoming the vehicle’s “brain” – orchestrating domains such as powertrain, infotainment, ADAS, and charging. In practice, it’s a data centre on wheels. The more performance, connectivity, and integration it has, the greater the cybersecurity challenges.
Modern vehicles blend multiple technology stacks – Linux for infotainment, Android Automotive for user experience, AUTOSAR Classic/Adaptive for safety-critical domains – all interconnected via networks like CAN, Ethernet, and LIN. Each stack has its own vulnerabilities, patch cycles, and dependencies. The result? A huge attack surface, with complexity amplified by zonal architectures and remote connectivity (Wi-Fi, Bluetooth, 5G, V2X).
Many vehicle features rely on third-party libraries or open-source software. These speed up development but can introduce vulnerabilities outside the OEM’s direct control. If a supplier delays a patch, the risk remains in the system until mitigated.
For engineers and architects, compliance is not just paperwork – it’s a design constraint.
The real challenge is embedding these into architectures that already juggle safety, performance, and cost targets – all under tight market deadlines. Non-compliance? The vehicle can’t be sold in many key regions.
Integrating security into established ASPICE-based development processes can be a challenging task. Cybersecurity tasks — such as code audits, threat modelling, and secure configuration checks – often add work that isn’t visible to end customers but is critical to system security and safety. Balancing these invisible tasks with delivery deadlines is a constant tension.
Security engineering rarely produces visible “features” for customers. Implementing secure boot, encrypting data at rest, or hardening an OTA pipeline takes significant time but doesn’t change how the car looks or drives. This can make it harder to justify resources internally – even though these measures are essential for protecting the brand and the user.
Attacks can target internal networks, external interfaces, hardware, or backend infrastructure. Real-world examples include:
These can be carried out by opportunistic thieves, organised cybercriminal groups, hacktivists, or state-sponsored actors – each with different capabilities and goals.
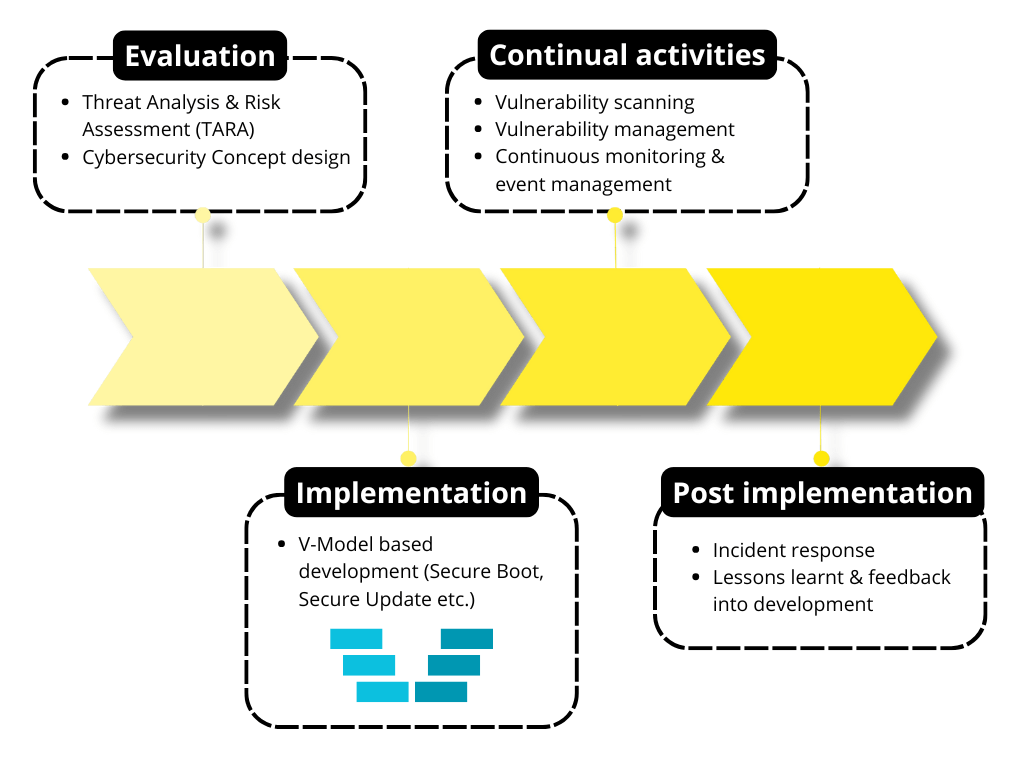
Automotive cybersecurity is a constant cycle of anticipating threats, building defences, and responding to incidents. It starts with TARA to identify where the highest risks are, from infotainment systems to safety-critical controls, guiding design priorities. Engineers then implement measures such as:
Security is validated through penetration tests, fuzzing, audits, and code reviews, all aligned with ISO/SAE 21434 and regulatory requirements. Increasingly, vulnerability scanning and management tools are integrated into the CI/CD pipeline, automatically scanning each build and feeding fixes into the development backlog – ensuring that known issues are addressed before they can be exploited.
After production (SOP), continuous monitoring via Intrusion Detection and Prevention Systems (IDPS) and Security Operation Centres (SOC) helps detect anomalies in real-time, ensuring readiness for the worst-case scenario.

Automotive cybersecurity is not a “feature” – it’s a continuous, evolving discipline that spans the full vehicle lifecycle: concept, development, production, operation, and decommissioning. It requires coordinated effort across OEMs, suppliers, regulators, and cybersecurity experts.
The vehicles of the future will be more connected, autonomous, and software-defined than ever before. Without robust, embedded security, they’ll also be more vulnerable. Getting it right isn’t just about compliance – it’s about safety, trust, and brand survival in the next era of mobility.
Sources:
The past few years have been challenging for the European automotive sector – production declines, supply chain disruptions, and intensifying competition from Asian manufacturers have forced many companies to downsize. Now, as the market slowly begins to recover, businesses face a new challenge: how to quickly restore their delivery capacity when skilled specialists are in short supply?
Read moreModern automotive lighting is no longer limited to a purely functional role. LED logos, illuminated grilles, and dynamic light animations are becoming a new communication language for car brands. How does the combination of design and technology turn light into a recognizable brand signature?
Read more